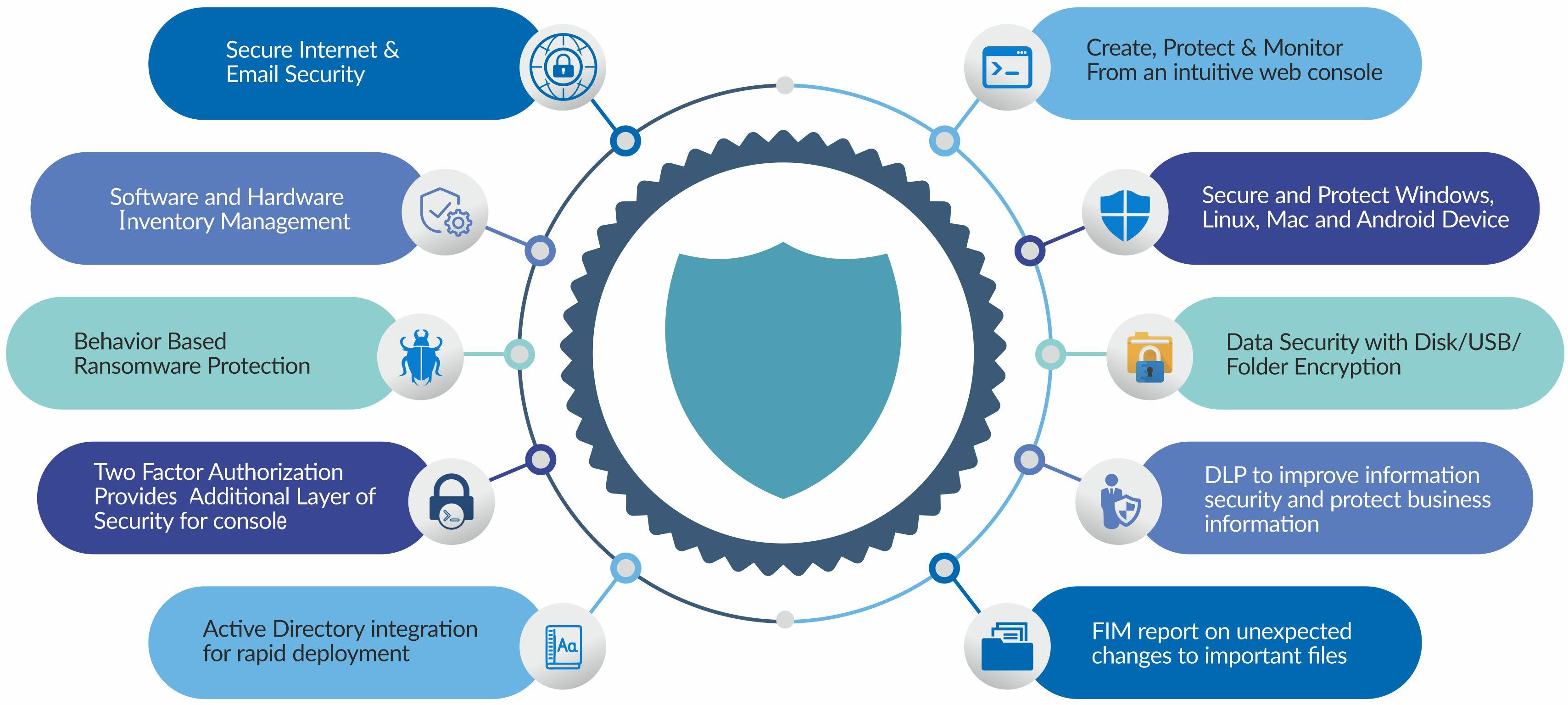
Deploy, Configure And Manage

Delivers a range of IT security services with scans on the
agent as well as on the Cloud that provide complete, in
depth protection against all forms of malware - whether
they originate from inside or outside the network via email,
sites, or the Internet. Connect securely to any device
Powered by Artificial Intelligence model, diligently
created Yara rules and Dynamic emulator leave no room for
any Malware to creep in.
With Secure Email Security Stop spam and secure incoming and outgoing emails and
suspicious attachments from infecting your device.
Enable Network monitor based on protocol/IP address, applications filter, block complete browsing or selectively add black and white list of web URLS,
restrict usage of web sites based on categories. Monitor internet and computer usage.
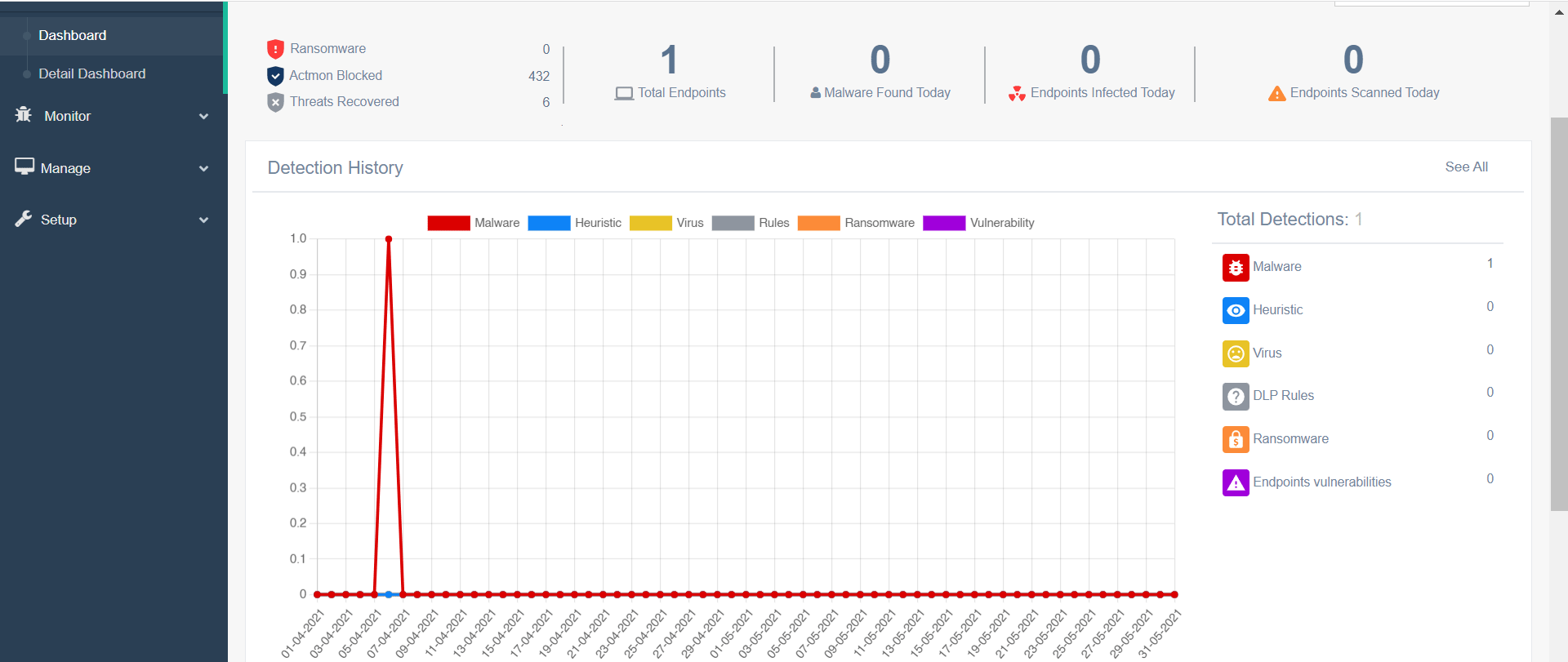
Manage your Endpoints wherever you are
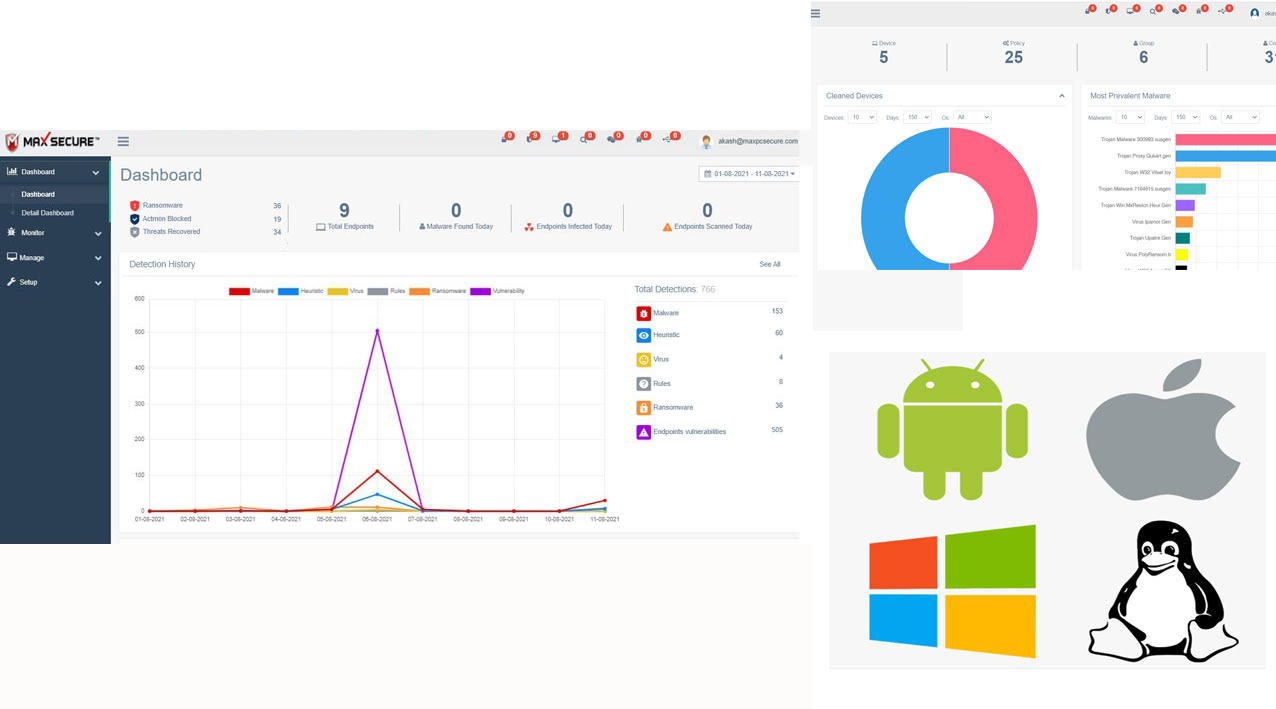
Create, Protect and Monitor
Web Console allows you to apply policies, configuration settings, application control, schedule updates, alerts, remote software installation and more
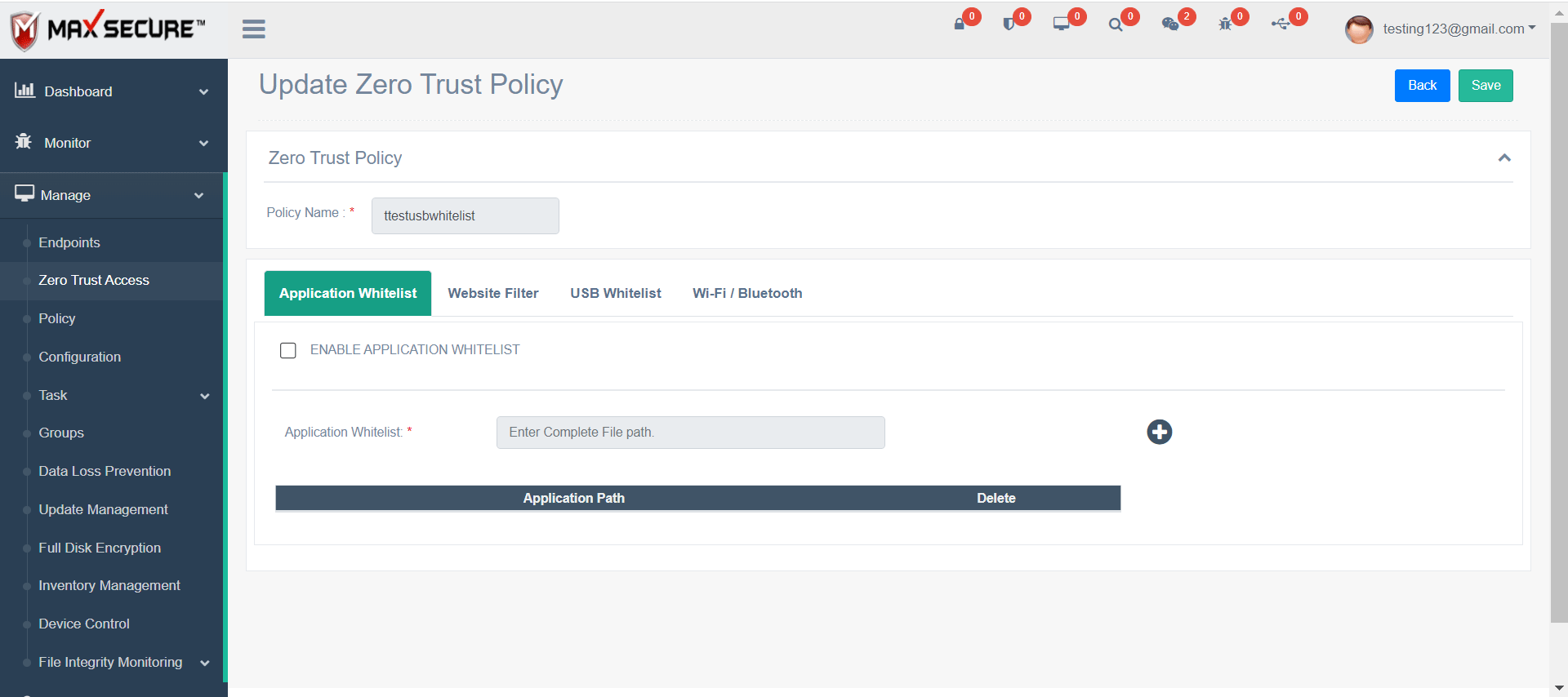
Zero Trust Access
Zero Trust means no application or web site or USB drive or Wi-Fi should be inherently allowed. With one click add Applications, Websites, USB devices and Wi-Fi that you want to white list, rest will be blocked. Or choose Block All option.
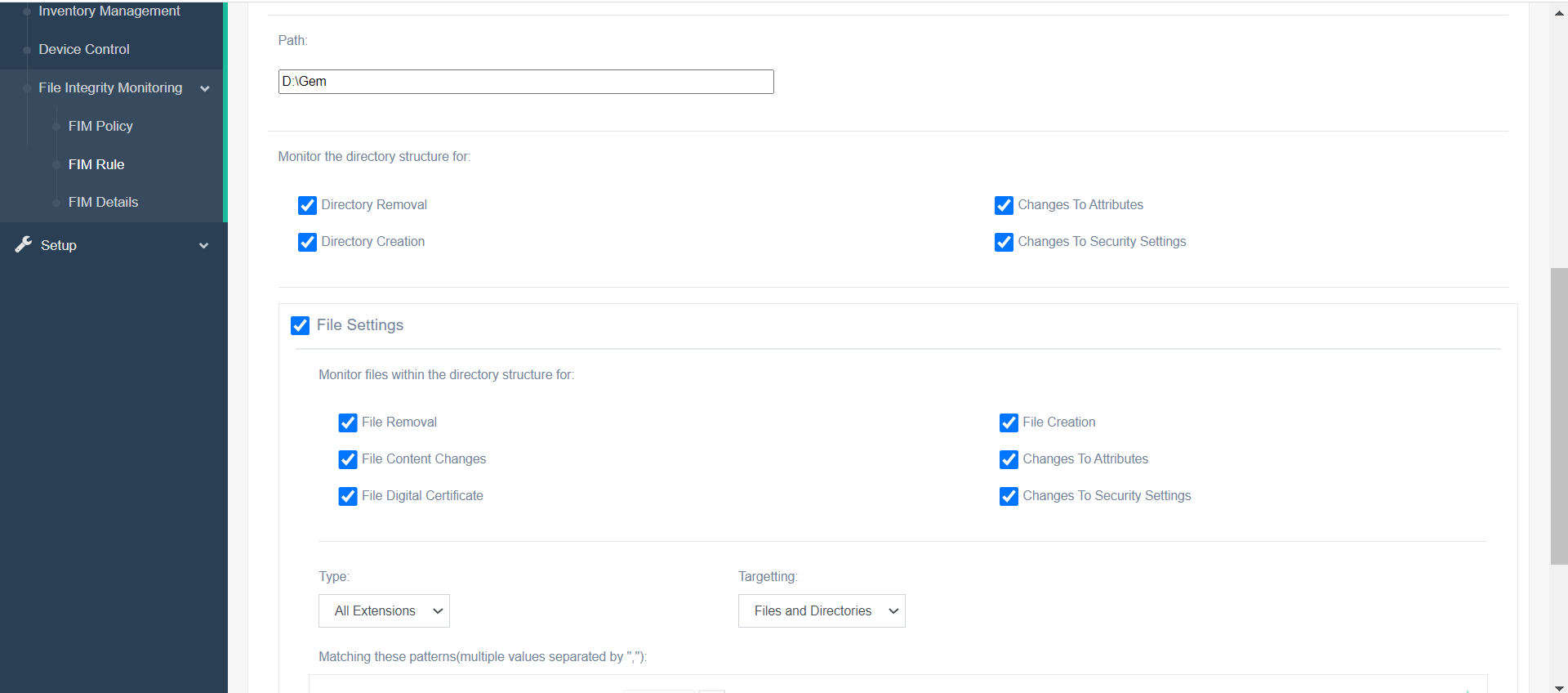
File Integrity and Monitor
Validates the integrity of an application software files or any directory/file using a verification method between the current file state with a known, good baseline.
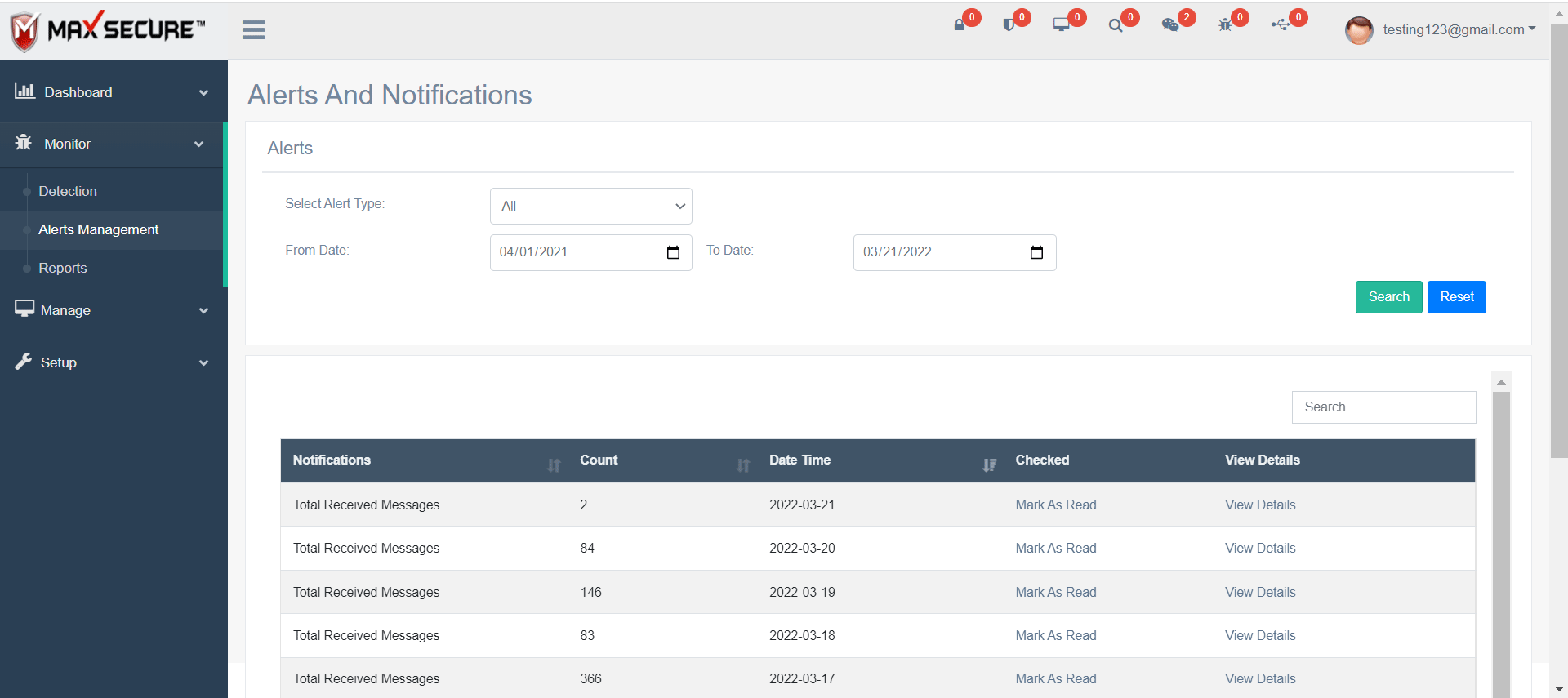
Update / Scan Schedule
Configure from Dashboard when you want to update and Scan client devices
Instant remediation
From Portal, add any new malware signature for immediate detection
False positive
Control, recover any false positives from the Portal.
USB Guard
Block Read / Write/ Execute, complete control on USB drive
Isolate infected Devices
Remotely remove the infecetd devices from the network
Ransomware Monitor
Block Ransomware as soon as they start encryption



OPERATING SYSTEMS
All major Windows Os above 8.0, Mac , Linux, Mac and Android versions
HARDWARE
500 MB of RAM available
1 GB of free hard disk space
Internet
Connectivity for Registration and Updates
BROWSERS
Internet Explorer 8 or later
Microsoft Edge 20.x – 25.x and later
Mozilla Firefox 52.x and later
Google Chrome 44.x – 52.x